What Is Oracle Database Vault?
The Oracle Database Vault security controls protect application data from unauthorized access, and helps you to comply with privacy and regulatory requirements.
You can deploy controls to block privileged account access to application data and control sensitive operations inside the database using trusted path authorization.
Oracle Database Vault helps you increase the security of existing applications by using least privilege best practices. Oracle Database Vault secures existing database environments transparently, eliminating costly and time consuming application changes.
Controls for Privileged Accounts
Privileged database accounts are one of the most commonly used pathways for gaining access to sensitive applications data in the database.
While their broad and unrestricted access facilitates database maintenance, the same access also creates a point of attack for gaining access to large amounts of data. Oracle Database Vault realms around application schemas, sensitive tables, and stored procedures provide controls to prevent privileged accounts from being exploited by intruders and insiders to access sensitive application data.
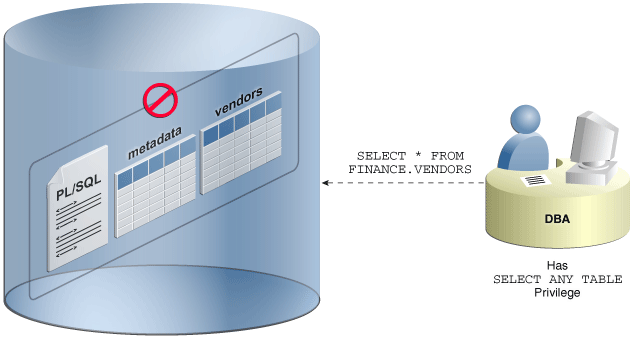
Fig1: Oracle Database Vault Realm Blocking DBA Access to Data”
Controls for Database Configuration
Common audit findings are unauthorized changes to database entitlements and grants of the DBA role to too many users.
Preventing unauthorized changes to production environments is important not only for security, but also for compliance as such changes can weaken security and open doors to intruders, violating privacy and compliance regulations. Oracle Database Vault SQL command rules enable you to control operations inside the database, including commands such as CREATE TABLE, TRUNCATE TABLE, and DROP TABLE. Various out-of-the-box factors such as IP address, authentication method, and program name help implement trusted path authorization to deter attacks leveraging stolen passwords. These controls prevent accidental configuration changes and also prevent hackers and malicious insiders from tampering with applications.
The Oracle Database Vault realms with the mandatory mode enables you to seal off access to application objects, even to those with direct object grants, including the object owner. With mandatory realms, you do not need to analyze who has access because this is clear from the list of authorized users
Enterprise Applications Protection Policies
Application-specific Oracle Database Vault protection policies and guidelines are available for major enterprise applications.
These enterprise applications include Oracle Fusion Applications, Oracle E-Business Suit, Oracle PeopleSoft, Oracle Siebel, Oracle Financial Services (i-Flex), Oracle Primavera, SAP, and Finacle from Infosys. Because Oracle Database Vault does not modify the application nor require changes to the client, you can use it with most off-the-shelf and custom applications.
What Privileges Do You Need to Use Oracle Database Vault?
Oracle Database Vault provides database roles that enable different users to perform specific tasks, based on separation-of-duty guidelines.
The most commonly used roles are as follows:
DV_OWNERandDV_ADMINenable you to create and manage Database Vault policies.DV_ACCTMGRenables you to manage user accounts.
When you configure and enable Oracle Database Vault, the DV_OWNER role is granted to a user who must exist before you begin the configuration process, and the DV_ACCTMGR role is granted to a second, optional user, who must also exist before configuration. You can grant the Database Vault roles to other users, but ensure that these users are trusted.
During the registration process, you must create backup accounts for the DV_OWNER and DV_ACCTMGR users. As a best practice, Oracle strongly recommends that you keep and maintain these backup accounts.
What are the Components of Oracle Database Vault
Oracle Database Vault has a set of components that include PL/SQL packages and other special tools.
- Oracle Database Vault Access Control Components
Oracle Database Vault enables you to create a set of components to manage security for your database instance. - Oracle Database Vault DVSYS and DVF Schemas
Oracle Database Vault database objects and public functions are stored in theDVSYSandDVFschemas, respectively. - Oracle Database Vault PL/SQL Interfaces and Packages
Oracle Database Vault provides PL/SQL interfaces and packages for security managers or application developers to configure access control policies. - Oracle Database Vault Reporting and Monitoring Tools
Oracle Enterprise Manager generates and maintains the Oracle Database Vault reports. - What Privileges Do You Need to Use Oracle Database Vault?
Oracle Database Vault provides database roles that enable different users to perform specific tasks, based on separation-of-duty guidelines. - Components of Oracle Database Vault
Oracle Database Vault has a set of components that include PL/SQL packages and other special tools. - How Oracle Database Vault Addresses Compliance Regulations
One of the biggest side benefits resulting from regulatory compliance has been security awareness. - How Oracle Database Vault Protects Privileged User Accounts
Many security breaches, both external and internal, target privileged database user accounts to steal data from databases. - How Oracle Database Vault Allows for Flexible Security Policies
Oracle Database Vault helps you design flexible security policies for your database. - How Oracle Database Vault Addresses Database Consolidation Concerns
Consolidation and cloud environments reduce cost but can expose sensitive application data to those without a true need-to-know. - How Oracle Database Vault Works in a Multitenant Environment
Using Oracle Database Vault in a multitenant environment increases security for consolidation.About Oracle Database Vault
The Oracle Database Vault security controls protect application data from unauthorized access, and helps you to comply with privacy and regulatory requirements. - Controls for Privileged Accounts
Privileged database accounts are one of the most commonly used pathways for gaining access to sensitive applications data in the database. - Controls for Database Configuration
Common audit findings are unauthorized changes to database entitlements and grants of theDBArole to too many users. - Enterprise Applications Protection Policies
Application-specific Oracle Database Vault protection policies and guidelines are available for major enterprise applications




