Introduction to Migrate to the Cloud
We have defined the process of moving “on-premise” applications, data and the related infrastructure resources to a cloud computing environment as “cloud migration”.
What are the traction elements that are driving today the enterprise world to a process of migration to a “CSP”?
- Money is the “nerf of war” often cost savings are the first driver.
- Application “Sarcophagus” moving a legacy application to a “containerized” or emulated environment waiting that a new deployment will replace it.
- Upgrading a data center environment with Cloud extension (hybrid).
- SaaS product evolution and a new licensing model.
- Managed environment services.
- Needs for specific regulatory or compliances, from the CSP (PCI, personal data, GXP, HIPPA, FINMA, ISO 27001, etc..)
- Access to global customers stretches out.
- Improved system availability and reliability, by the implementation of managed cloud infrastructure.
- Defined new security and compliance services and level for new deployment in the Cloud.
- Cloud Disaster Recovery.
- Cloud backup solution, leverage archiving solution model.
- etc…
At the end each organization will have its own drivers and will be in a different cloud journeys, buzzing words will certainly ring the bell for most of them (cloud-agnostic, multi-cloud containerization, DevOps, DevSecOps, microservices, FaaS, etc…), that could certainly create the biggest impact of resistance instead of adoption, maybe due to the arrogance expressed by the CSP services and people, (old world vs new world).
Regardless of the driver, the migration phases remain common to each successful migration to the cloud; they are the basis of the best migration practices to the cloud recommended by the CSPs.
These phases, based on experience and acquired knowledge, have made it possible to develop the base necessary for the development of best practices or white papers collected from various organizations that have successfully migrated their IT platforms to the cloud.
Best Practice Migration Methodologies
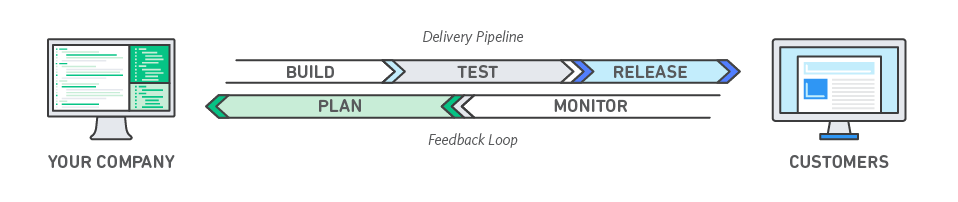
Each organization considering a potential migration of its existing infrastructure to the cloud is encouraged to adopt these best practices, which can be adapted to meet the individual needs of an organization.
Step 1: Business Planning requirement & Migration Preparation.
Any project starts with a need, with sponsors and stakeholders support certainly part of the steering group, a budget, a business reason, a deadline and above all a business goal to achieve.
In our context, we speak of migration to the cloud, often pushed by management, often refused by middle management supported and helped by analyzes of any kind, valid or not.
This phase is crucial and unfortunately often will be the door to the refusal of many entities (security in general, operation, cost management, opex model, etc…)
To be successful, the organization will need sponsorship from senior executives to develop and approve a cloud strategy around the chosen CSP (s).
But here the stake is too great, many organizations have already demonstrated that the implementation of the cloud and its derivatives could generate significant costs and that many implementations have already returned to private data centers.
The reason is that the implementation of cloud strategies and infrastructure has often been operated in the known model that of “conventional” IT, I would come back to a simple metaphor, “nobody wants to have their cheese stolen”.
What is the CCoE “Cloud Center of Excellence“?
Using a Cloud Center of Excellence: (Source: AWS).
This is your first step to create a cloud dedicated team and to be honest, it can be part of people actually driving your IT, but be careful in the selected people it could be the best way to create a failed cloud migration strategy.
These persons will need to have a certain level of cloud maturity and a certain level of management they have to be ready to analyze, manage and engage with CSP and cloud partner, it is of course not a question of age but of mindset.
The team could consist of the below roles types and will be responsible for defining the security, availability, compliance, and reliability objectives for the migration to the cloud:
- Cloud strategy and business manager.
- Cloud Lead architect.
- Cloud infrastructure engineers.
- Cloud Security engineers.
- Cloud Application engineers.
- Cloud Operations engineers.
Step 2: Discovery planning & identification of cloud usual suspect.
To enable the successful migration of workloads from private data centers to your CSPs, it is mandatory to understand the complexity, the interdependencies of the applications and the level of dependence of the company on these selected workloads. it is also important to collect data on resource usage, configurations, and their behavior patterns. Of course, this analysis will have a total financial aspect of ownership (TCO) of the execution of the workload on the CSP which will form the future migration strategy, including the execution plans.
Start with Quick Wins, selecting the complex business-critical application is maybe not the first target for your cloud migration today, be a realist and give the chance of your team, your consultant, your cloud partner and before everything your IT to understand adopt, test and verify the cloud capabilities of the CSPs.
A first migration or plan could start by migrating the less critical and standalone applications using lift and shift, “Yes lift and shift” as it can be seen as an easy process for migration, but I will ensure that major party of these persons concerned by the migration has never touched any kind of this process by their own.
The goal is to build confidence within the team and the business stakeholders and also establish guidelines for future migrations.
The second major plan will be the discovery of the “Shadow cloud deployment”, as usual, you will maybe discover thousand of applications already hosted in the cloud completely out of any security compliance scope.
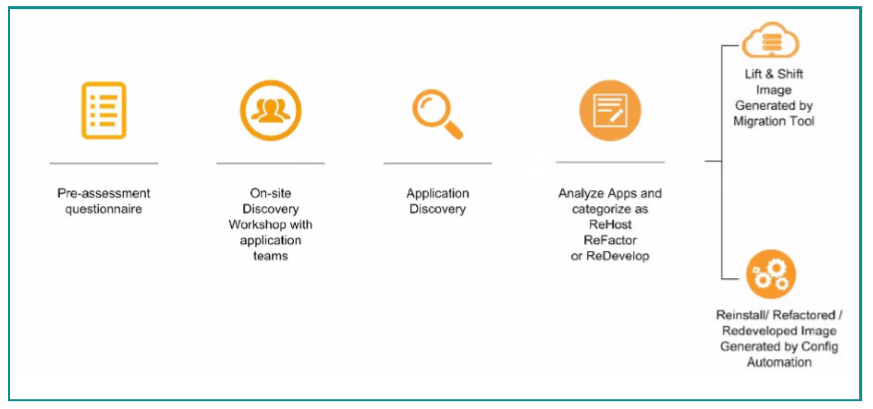
Assessment and Application Discovery.
Assessment can, of course, be done manually that include the ability to obtain the most up to date information (CMDB) related to the application you’ve selected, another option is to use agent tools (agentless or not) to collect, analyze create application map inherency, usage, sizing, latency, workload usage of the targeted application, I could give a lot of tools that could help you to build this analysis, let’s cover that point later on.
We’ve started with a lift and shift target don’t forget that in an on-premise workload we were designing the solution to handle the increase of the workload normally on 3 years, cloud elasticity is the first step to build a scalable elastic infrastructure able to react to the application demand, in short term, test and validation will give the targeted environment (instance container) and give the selected model of the deployment the capacity to sustain the business needs.
I will introduce here a name, re-platform or refactor that could be a first good step in the adoption of cloud using managed cloud services coming from the CSP by example migrate your MySQL, PostgreSQL, and SQL Server DB to a managed CSPs version (Azure SQL Database, AWS RDS or GC SQL).
Step 3 – Designing a new cloud infrastructure.
How is your security layer in the cloud?
We have found the right target for our migration, we have planned a migration strategy with timeline, implemented a team followed by a Cloud project manager that build and follow the schedule, this project must be carried out with agile methods which engage each of the participants in “sprints”, where milestones must be reached at regular intervals.
As explain the migration strategy can be an application re-design or could be a re-factoring infrastructure design or more simply a reinstall that will need application update and OS migration.
The procedure to implement a secured cloud layered infrastructure will be your warranty for the future test and verification of the security and compliance of the migrated application
After the cutover deadline defined you will have to implement a post-migration test plan that will be part of the overall migration process.
@Hitachi Vantara we recommend that every migration use the Secure Cloud Computing Architecture (SCCA) published by the Defense Information Systems Agency (DISA) as a benchmark reference (see Figure 2).
This framework covers all aspects of public cloud implementation and helps prioritize security concerns inherent in today’s infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS) and software-as-a-service (SaaS) industry offerings.
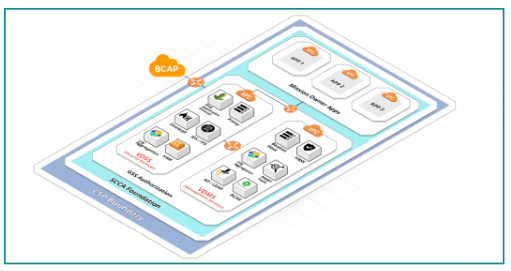
How is your Landing Zone ?
Your on-premise workload or targeted application will land in a CSP selected infrastructure but have you started the process to verify the compliance and security level of it?
The first assessment as to be this one, for this purpose you will have to engage with a specialized partner able to give you the targeted defined perimeters definition.
Step 4 – Migrating & Validating Applications
Database and Server Migration
-A massive part of the infrastructure you will target to move is certainly based on VMware.
-Coming directly from the CSPs or service providers like Hitachi Cloud Consulting, there are already several possibilities to connect and migrate in an automated and secure way your on-premise vSphere workloads directly to the CSPs.
-The migration of your on-premise DB must be quick and secure, while the source database as to remains fully operational during the migration.
Migration DB design plan migration must support both homogeneous migrations (e.g. MySQL on-premise to MySQL on CSPs) and heterogeneous migrations (e.g. PostgreSQL on-premise to Microsoft SQL Server on CSPs DB).
Data Transfer leveraging Object-Storage
-Using Object storage technologies and REST API (blob services, S3, Google cloud storage bucket) will bring you several options to transfer data from your on-premise to your bucket repository.
-CSPs are providing a large number of tools that will facilitate the transfer of on-premise datastore to storage services.
Continuous Improvement:
Now integrate a continuous improvement methodology and review the design, migration and validation phases to get the applications fully operating on.
Conduct a Post Implementation Review (PIR) for each migrated application it is recommended to ensure the learning is carried on to future application migrations.
Step 5: Change Your Operating Model
-Setting up a hybrid IT infrastructure (on-site and in the cloud) integrating the migration of applications or the creation of new ones (cloud-native) to the Cloud will require an overhaul of the operating model of the organization to get the most out of the cloud environment.
-Based on the IT model used to run an on-premises environment to a more agile cloud environment, this will limit the potential to take full advantage of the migration.
-For the best performance possible in this migration will require a combination of people, processes and technologies that will manage the IT fleet after the migration. It will have to evolve and improve continuously as migration accelerates.
This new setup will bring you the possibility to encompass new process and technologies as described below:
DevOps & DevSecOps definition:
–DevOps is a combination of cultural philosophies, practices and tools that improves a company’s ability to deliver applications and services at a high rate.
-It enables products to evolve and optimize faster than companies using traditional software development and infrastructure management processes. This speed allows companies to better serve their customers and gain competitiveness.
-It focuses on principles such as: infrastructure as code, continuous deployment, automation, monitoring and security. CSPs (AWS Azure, Google) provide a wide range of DevOps tools and also support the use of third-party products to help organizations comply with these principles.
-Native services can be used to create a fully automated continuous integration and continuous deployment (CI / CD) pipeline for software creation, testing, and deployment.
In some DevOps models, quality assurance and security teams can also be tightly integrated into development and operations, as well as the entire application lifecycle. When security is at the heart of a DevOps team’s activity, we talk about DevSecOps.
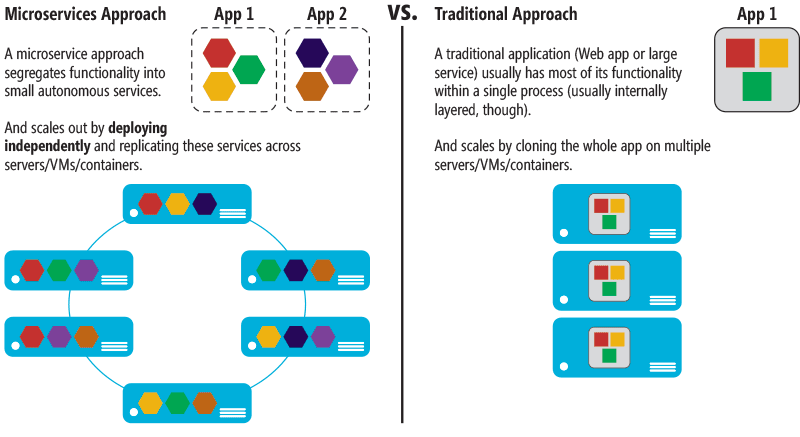
Microservices
A common approach to reducing operational efforts for deployment is container-based deployment.
Container technologies like Docker have increased in popularity in the last few years due to benefits like portability, productivity, and efficiency.
The learning curve with containers can be steep and you have to think about security fixes for your Docker images and monitoring. by example: Amazon Elastic Container Service (Amazon ECS) and Amazon Elastic Kubernetes Service (Amazon EKS)eliminate the need to install, operate, and scale your own cluster management infrastructure. With simple API calls, you can launch and stop Docker-enabled applications, query the complete state of your cluster, and access many familiar features like security groups, Load Balancing, Amazon Elastic Block Store (Amazon EBS) volumes, and AWS Identity and Access Management (IAM) roles.
AWS Fargate is a container management service that allows you to run serverless containers so you don’t have to worry about provisioning, configuring, and scaling clusters of virtual machines to run containers. With Fargate, you no longer have to worry about provisioning enough compute resources for your container applications. Fargate can launch tens of Amazon Web Services –Implementing Microservices on AWSPage4thousands of containers and easily scale to run your most mission-critical applications.
Sources: AWS
Serverless computing
Serverless computing does not eliminate servers but aims to relegate questions related to computing resources to the background during the design phase.
The term is often associated with the NoOps (No Operations) movement and the concept is also known as FaaS (Function as a Service) or RaaS (Runtime as a Service).
The AWS Lambda service is an example of serverless computing in a public cloud.
Developers can enter code, build backend applications, create event management routines and process data, all without worrying about servers, virtual machines (VM, Virtual Machines) and computing resources underlying components necessary to support a very large number of events, as the hardware and infrastructure are managed by the supplier.
Example: AWS Lambda can also interact with many other Amazon services, allowing developers to quickly build and manage complex enterprise applications with little or no concern for the underlying servers.
Serverless is a usual suspect for security improvement.
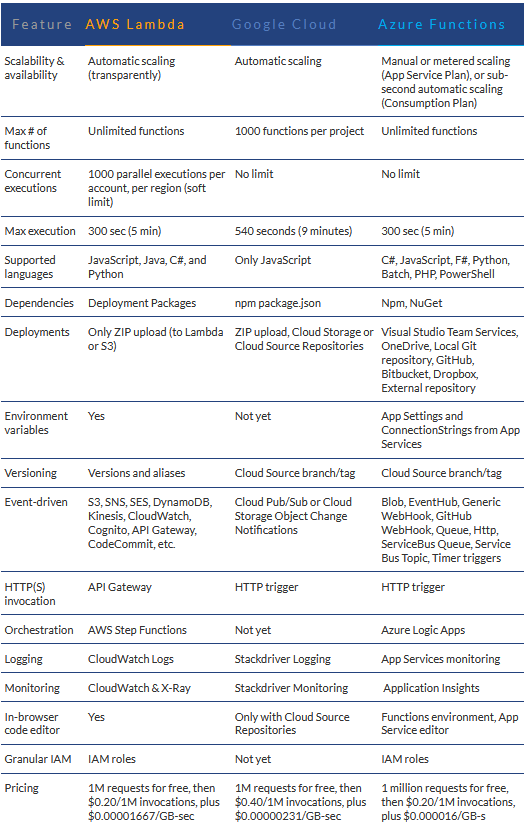
Serverless CSP Comparison:
Microsoft Azure Functions vs. Google Cloud Functions vs. AWS Lambda
Being Cloud well-Architected Framework:
Hitachi Vantara developed the well-architected framework based on best practices and core strategies for architecting systems in the cloud.
We “industrialized” this methodology reusing secure and compliant layers and blueprints like the SCCA DoD Cloud Computing Security Requirements Guide (CC SRG) Impact Level (IL) 2, 4, 5, and 6, leveraging our own developed platform coming from the REAN acquisition now named HCAP Hitachi Cloud Accelerator Platform.
Using this framework, organizations can evaluate their cloud architecture and come up with a set of remediation activities that can be implemented to harness the power of each CSPs most efficiently.
Conclusion
Cloud Migration Services from Hitachi Vantara have delivered end-to-end cloud strategies and architected and implemented solid cloud foundations for a number of large enterprise customers across a variety of regulated industries. These engagements have helped organizations overcome key challenges and realize more predictable cost structures, better use of modern technologies, greater innovation and increased productivity.
The U.S. Transportation Command, SAP NS2, American Heart Association, Ditech and Radian Mortgage started their cloud journeys early on and have completely transformed their organizations by putting the right foundations in place.
Sources: Hitachi Vantara
–